The true story of my first “intrusion” using dial-up internet.
The beginning 101
In mid-2004, access to the internet was still difficult and expensive for most people, Windows Live Messenger (MSN) was the most popular application for most teenagers in my city, at the time, and the chat rooms in the IRC were already losing clients.
My internet access was through dialers, where the maximum was 56 kpbs. That gave me access to MSN, P2P networks and eventually search random sites, curiosities, videos no way, it took days to download a single clip.

During my browsing, I started to come across Website defacement1, a peculiar type of attack where the attacker unauthorizedly alters someone’s website, usually in order to give himself some kind of fame or write some message, and that caused curiosity, which made me delve into the subject of security vulnerabilities.
Choosing the victim
Deciding to carry out an intrusion test, the objective was to gain remote access to someone else’s computer, but I would have to choose a victim who could be “collaborative” during the process as I needed a few steps to make this possible, One of the factors was that the victim did not have antivirus or that if there was, it could be temporarily deactivated. After some explanations, a friend agreed to be the “victim”.
The evil tool belt
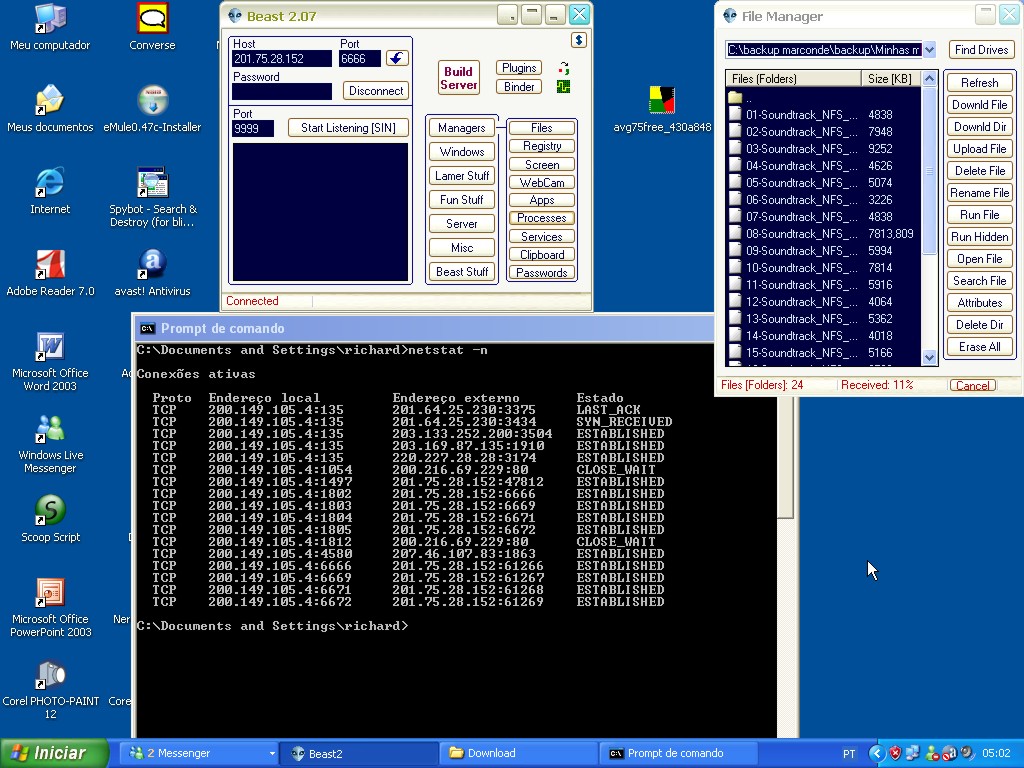
The way I chose to perpetrate the intrusion was through the trojan called Beast2, in addition to being a Remote Administration Tool 3(RAT), it also had binder functions which I used to mix (binder) the beast server which was an executable file, with a jpg photograph, that way I could trick the MSN servers and send it through a conversation, and it was easier to convince someone to click, an image… why not?
The second step was to discover the valid IP of the “victim” machine. Back then, the internet was not as complex and secure as it is today, and during a transfer of any file via MSN, netstat at the right time could give us this information.
With the server running, after all our “victim” opened the “photo”, we had the IP, just pasted it into the host address, entered the configured password and connected.
I’m in, what to do?
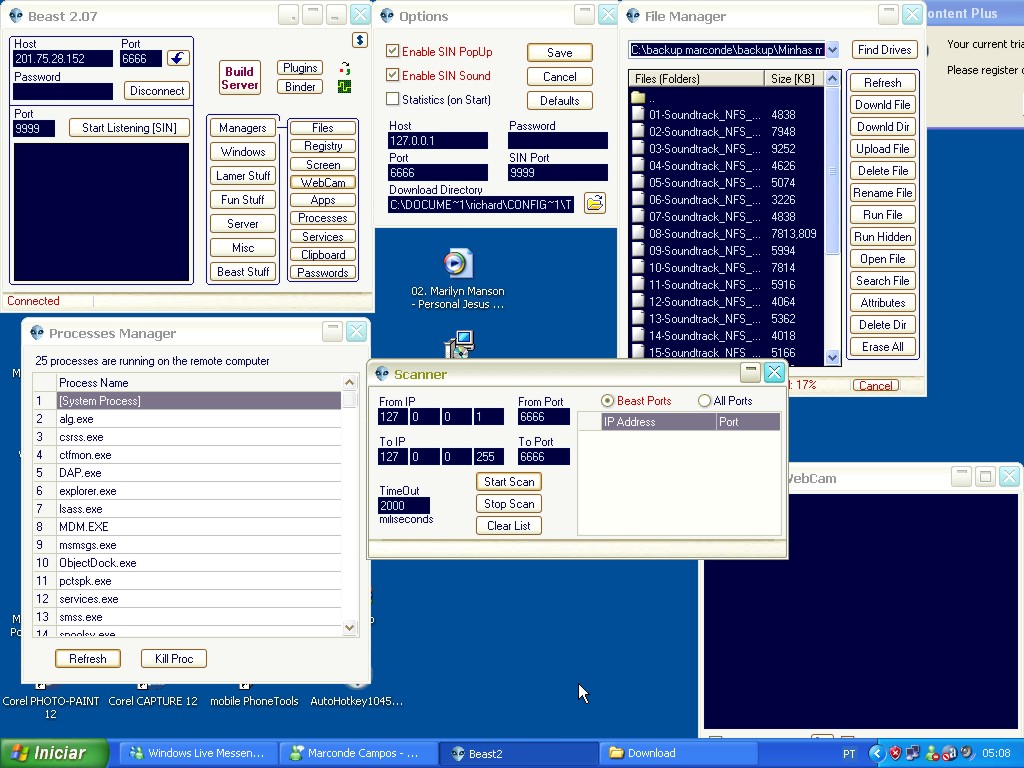
After connecting successfully, we spent long hours playing with some of the interesting functions and validating everything that was happening through MSN.
Functions such as controlling the mouse arrow, even without seeing the victim’s screen or sending Windows error with personalized text, to more serious things such as listing processes and even executing or ending something.
This gave me real-time feedback on what really worked in the program, and what the victim’s impressions were regarding everything, I was able to download some files, and even collect some information from the target machine.
Until that moment we had no idea if there was another directory in which the malicious program hid a copy of itself, or opened connections to third parties besides the main attacker and the test was completed by disconnecting from the victim’s machine and starting an antivirus scan. , which automatically identified and deleted the file within minutes.
Thanks for this post go to my colleague Marcodes Campos, who offered to help during the process.
References
Leave a Reply